Securely Chaining Routers
Building a Home WiFi Network
Putting together a home network has several subtly annoying security tradeoffs.
Users want
-
Ease of Use & Connectivity
Maximized by keeping devices maximally connected with a simple passphrase
-
Privacy and Security
Maximized by keeping devices minimally connected. And ideally offline 🦦
If the goal is a bit of both, how to do segmentation correctly quickly becomes a bit of a puzzle
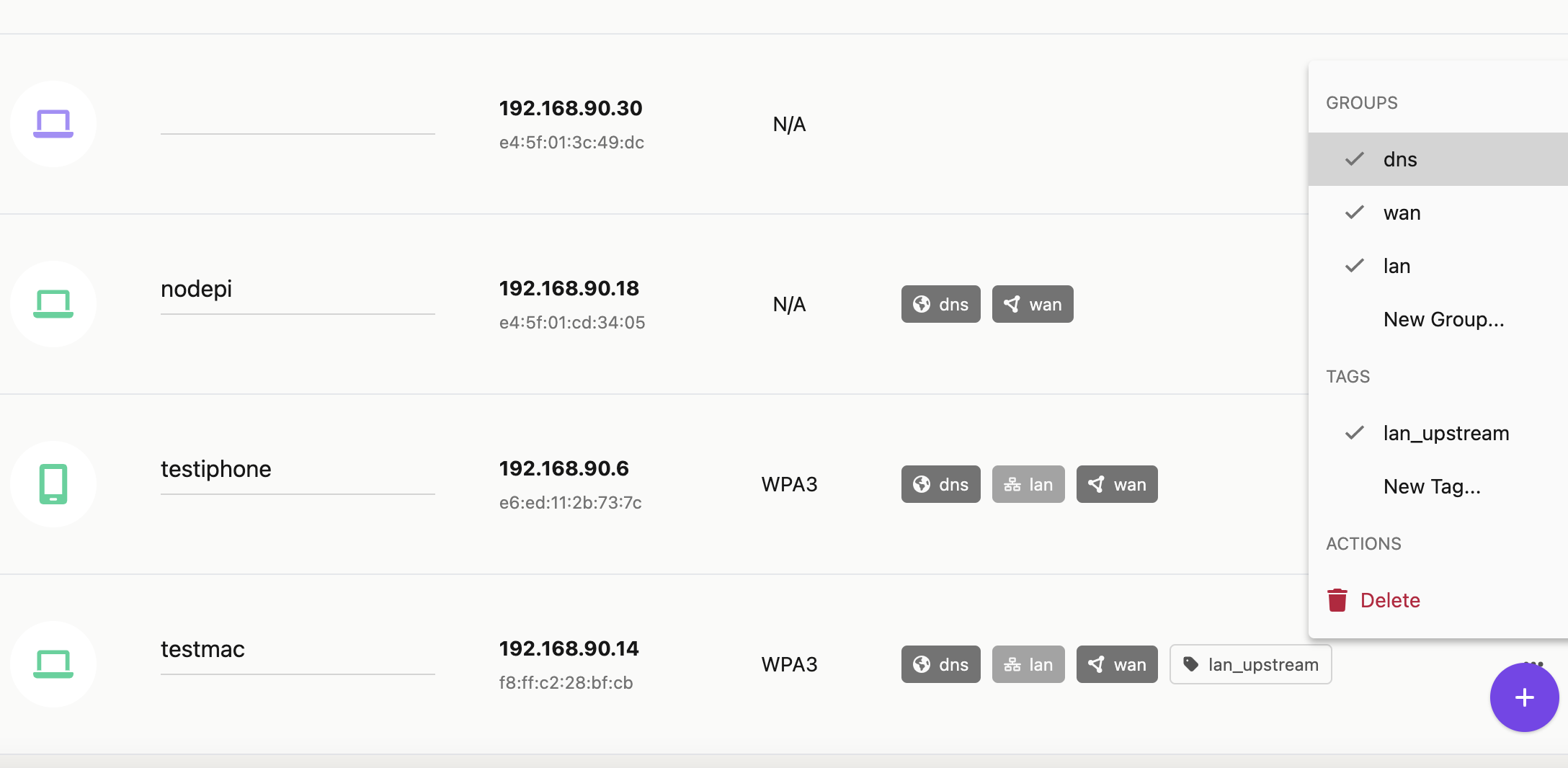
What's the Best Way to Chain Your Routers?
The "Secure Router" can be considered the Work From Home access point, and the "Guest Router" can be considered the Guest, Personal, or IOT access point.
The Worst Choice
Option #3 is to connect the internet to the secure router, and then plug the guest router into the secure router. Guests and untrustworthy devices can connect to the guest router.
This might make sense intuitively for some. You put the Secure Router close to the internet since that's where all the internet traffic will go out from, and if the Guest Router is compromised, it can't intercept traffic.
However, since the Guest Router is a Peer on the Secure Router network's LAN, every "Guest" station and the router will be able to reach the secure router and devices on the secure network LAN.
Unless either the Guest Router can block requests to the Secure LAN with its firewall, or the Secure Router can isolate the port for the Guest Router for only internet access, this is not an accepted best practice.
Split ESSIDs
Option #1 is to share a router for both SSIDs, with one ESSID and password for the Secure LAN and one for the Guest LAN.
The expectation is that devices can not send packets across the two LANs.
The great tradeoff with this is that if a user wants to control their IOT devices they have to switch to the guest network. And if device isolation is enabled on the guest network, devices won't be able to communicate at all. So as security improves, usability decreases.
The guest isolation may also be insufficient. The shared passphrase implies MITM capabilities, and passive traffic decryption capabilities with WPA2 or active decryption capabilities with WPA3.
Some routers place both ESSIDs on the SAME LAN. Usually this allows the secure devices to reach the guest devices. Usability has been increased, but this often leads to subtle flaws that allow the guest devices to bypass their isolation entirely.
Another upside to this approach is that bandwidth can be shared for the ESSIDs, reducing wasted WiFi spectrum.
Overall, this is an accepted best practice, but it comes down to the details where very quickly users are trading off security for usability.
The Best of the Three: Guest Router First, Secure Router Second
Option #2 is the recommended and accepted best practice. The Guest router connects directly to the internet, and the Secure router plugs into the Guest Router.
This approach yields a favorable combination of security and usability. Devices on the secure LAN can access devices on the Guest LAN, which is great for controlling IOT devices. And devices on the Guest LAN have no way to initiate communication to devices on the Secure LAN, blocked by the Secure Router firewall.
The main downsides: The guest router could have ISP credentials, and could MITM internet traffic if compromised by an untrusted device.
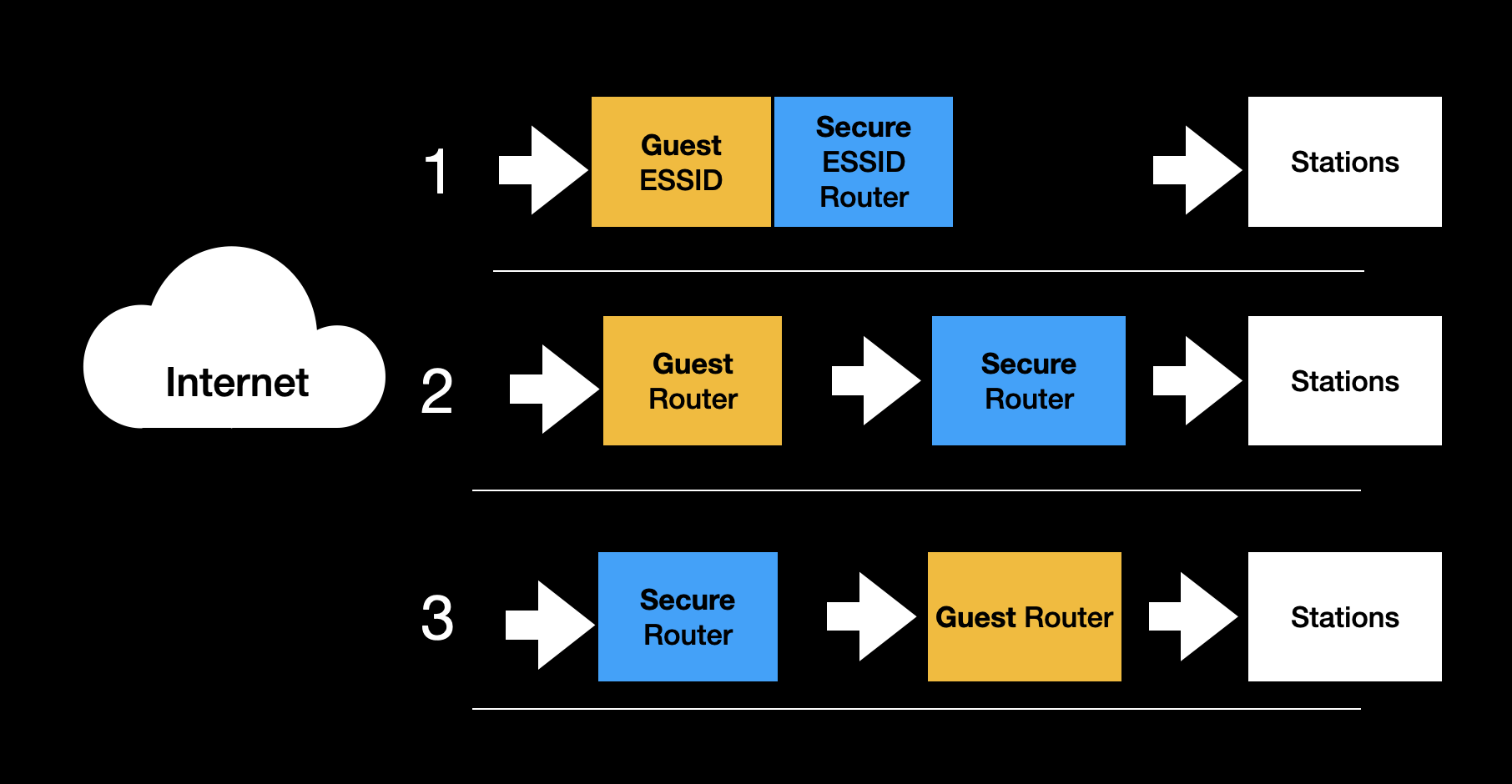
Multi PSK & VLANs
Today's most featureful home routers offer support for one passphrase per device. This solves many of the MITM and decryption issues for guest isolation. The devices can be placed into VLANs with unique WiFi passphrases, GTKs, and secure firewall rules creating truly strong isolation. These mechanisms provide powerful mechanisms for designing a home network securely.
This is the approach SPR follows, and we've spearheaded Multi-PSK with WPA3. SPR provides maximum isolation capabilities by placing each station into its own LAN. Users can then easily create groups of interconnected devices.
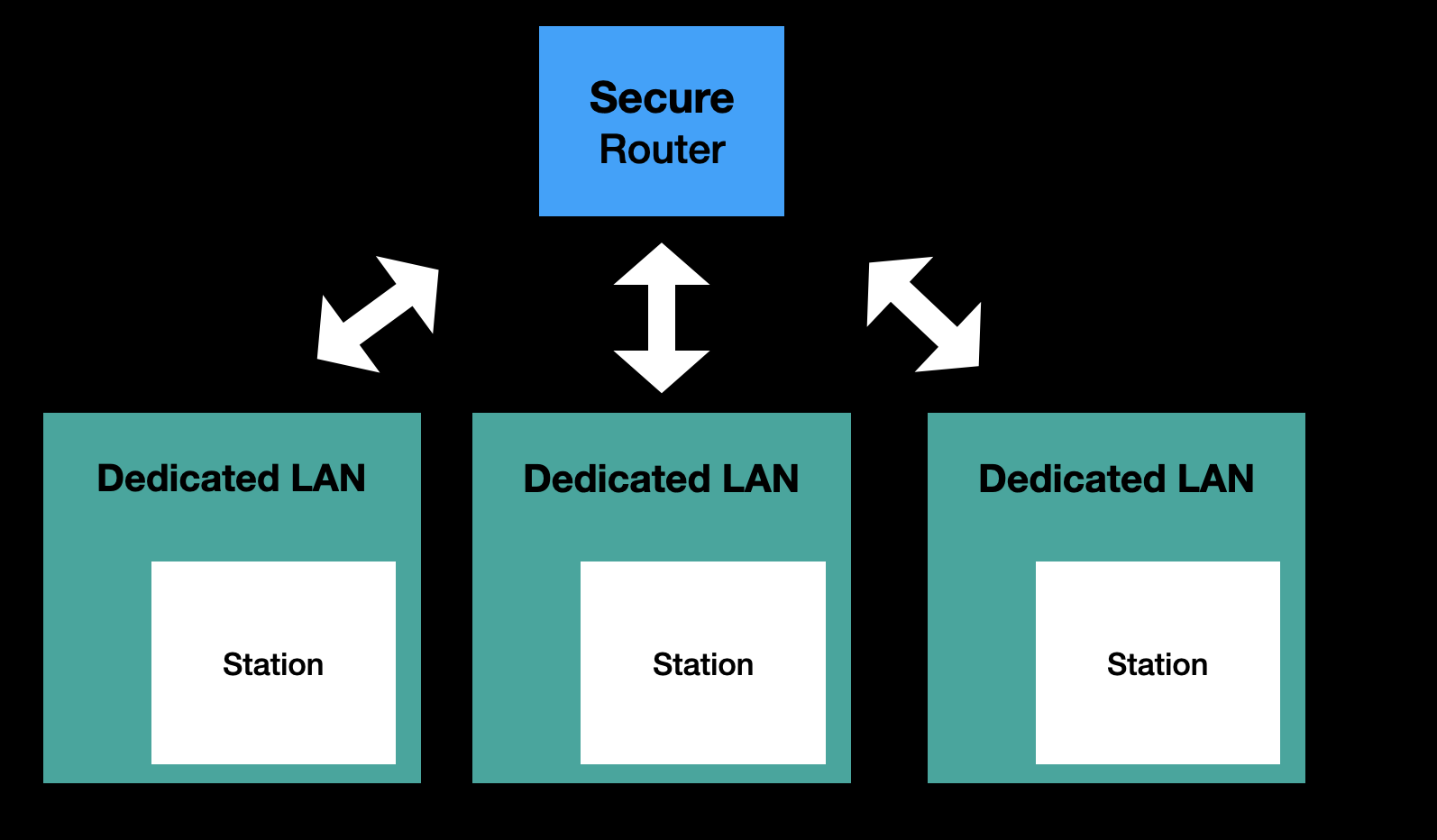
SPR Supports Plugging into An Existing Router Securely
We recommend running SPR by plugging it into an existing router. To support securely doing this, by default -- the firewall will block access to private network addresses over the upstream interface.
This prevents devices connected to SPR from accessing devices on the LAN of the current router.
To allow a device access to private network addresses upstream, users can apply the lan_upstream tag to the device.
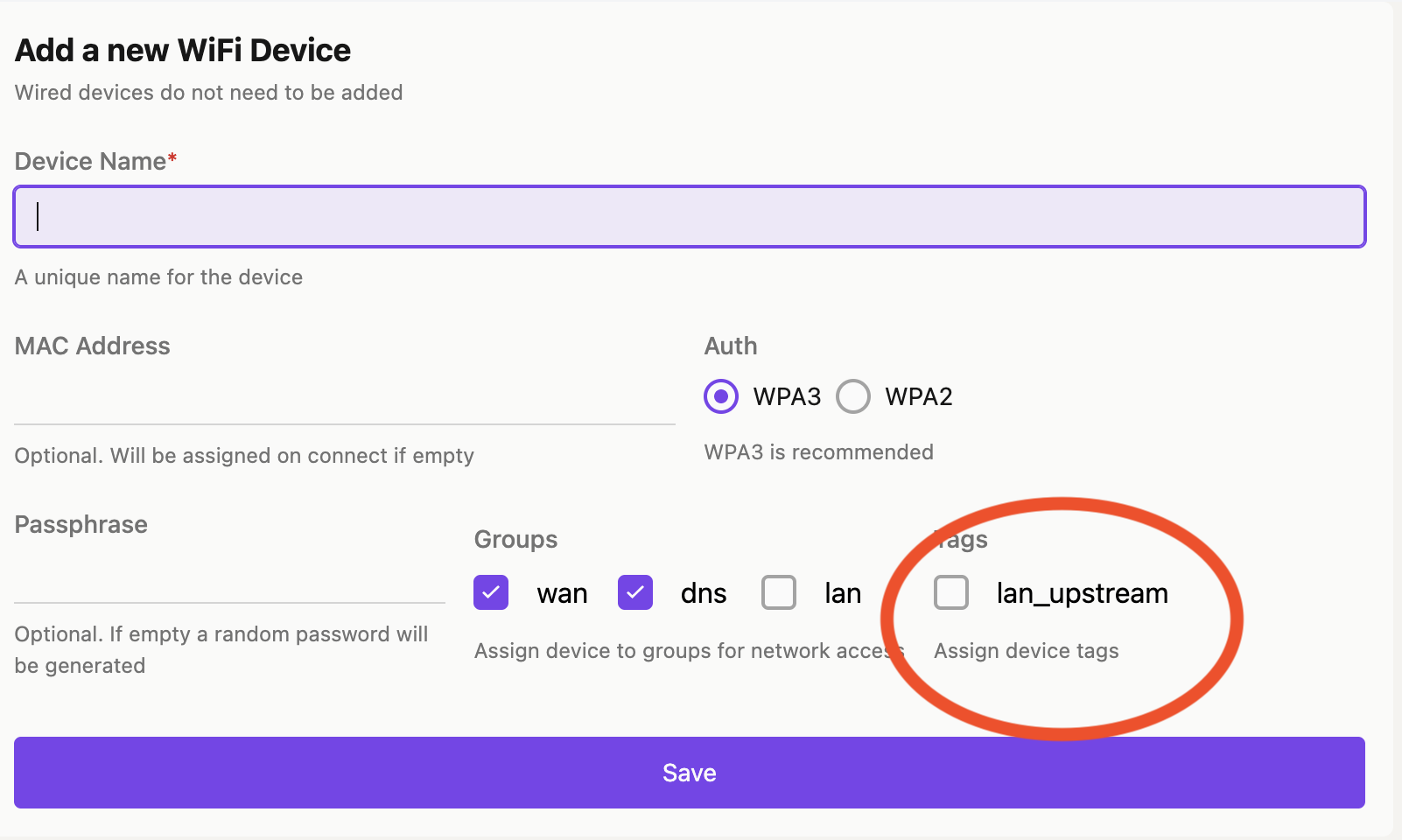
And then manage the tag in the Devices view