What the I-Soon Leak Tells Us About WiFi Hacking
The I Soon Dump
"The documents come from iSoon, also known as Auxun, a Chinese firm headquartered in Shanghai that sells third-party hacking and data-gathering services to Chinese government bureaus, security groups and state-owned enterprises. "
The Washington Post writes that "The documents show that iSoon met and worked with members of APT41, a Chinese hacking group that was charged by the U.S. Justice Department in 2020 for targeting more than 100 video game firms, universities and other victims worldwide."
WiFi Capability: Hardware Implants
The dump has a product catalogue that starting from page 18, describes hardware implants for persistent access to target environments. These implants are used for accessing a victim network without having to evade outbound proxies or firewalls, where security monitoring might take place. So they can attack the squishy inside directly.
They communicate to targets over WiFi and exfiltrate over 3G/4G.
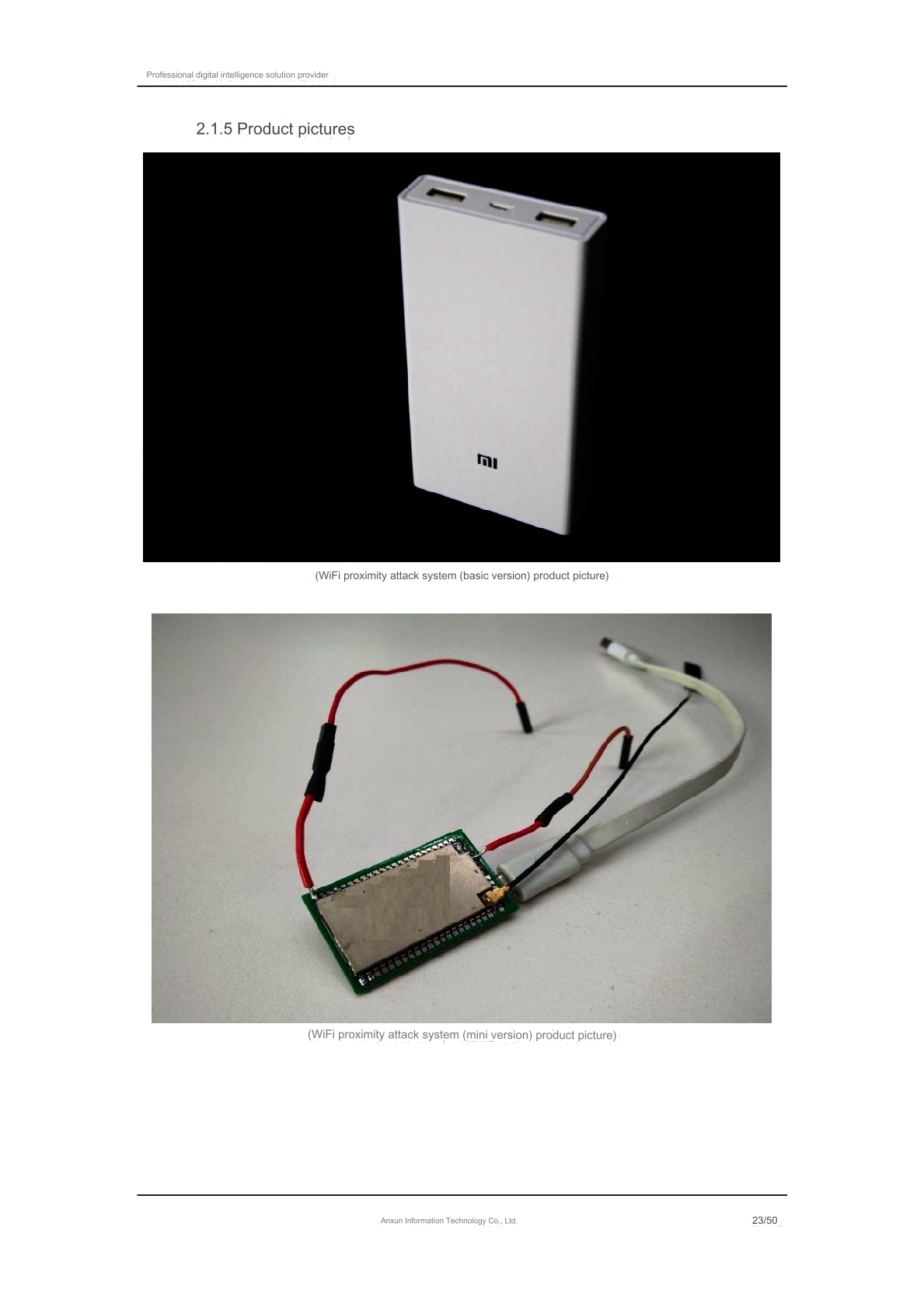
- They are small, portable, and have 3G/4G internet connectivity
- They can be powered or run on a 10A battery that lasts 8-20 hours depending on activity
- They can be embedded into a decoy power bank or other device
WiFi Attack System
Attackers can also connect into the sensors over 4G connectivity and then attack the environment over WiFi. It has standard capabilities one finds in tools like Kali Linux.
- WEP/WPS/WPA/WPA2 cracking
- Cracking can also be done via a more powerful cloud system
- Once on a network the device can inspect packets for hashes
- Once on a network the device can brute force login credentials for routers
- The device can proxy traffic to the local network
Uniquely:
- The device can self destruct
What's Not in The Dump
What we don't see a cache of ready to go router exploits, patched or unpatched, as well as software/firmware capabilities for unpatched IOT devices which are soft targets on wifi.
Closing Thoughts on Detection
- Nothing in the documents hits on masquerading implants by MAC address. A good asset inventory might go a long way when the device joins the network
- Tools like Nzyme can help detect WiFi Cracking attempts as well as detect rogue APs in the environment. SPR supports nzyme taps
- Building a baseline of WiFi APs would be the best way a defender can detect a WiFi Implant entering the environment
- Defenders need internal network sensors as well as sensors on the outbound network
- A zero-trust network setup would help mitigate this type of implant reaching an asset's networked resources, but would still leave client devices vulnerable to Rogue AP attacks unless they employ zero-trust principles for WiFi connectivity (like EAP-TLS/EAP-TTLS or per-device WPA3 personal passwords)