Authentication, Association, and Authorization in 802.11 WiFi
Association in the 802.11/ WiFi World comes in the "loose" variety of the term, and why Hostapd disconnect events are confusing...
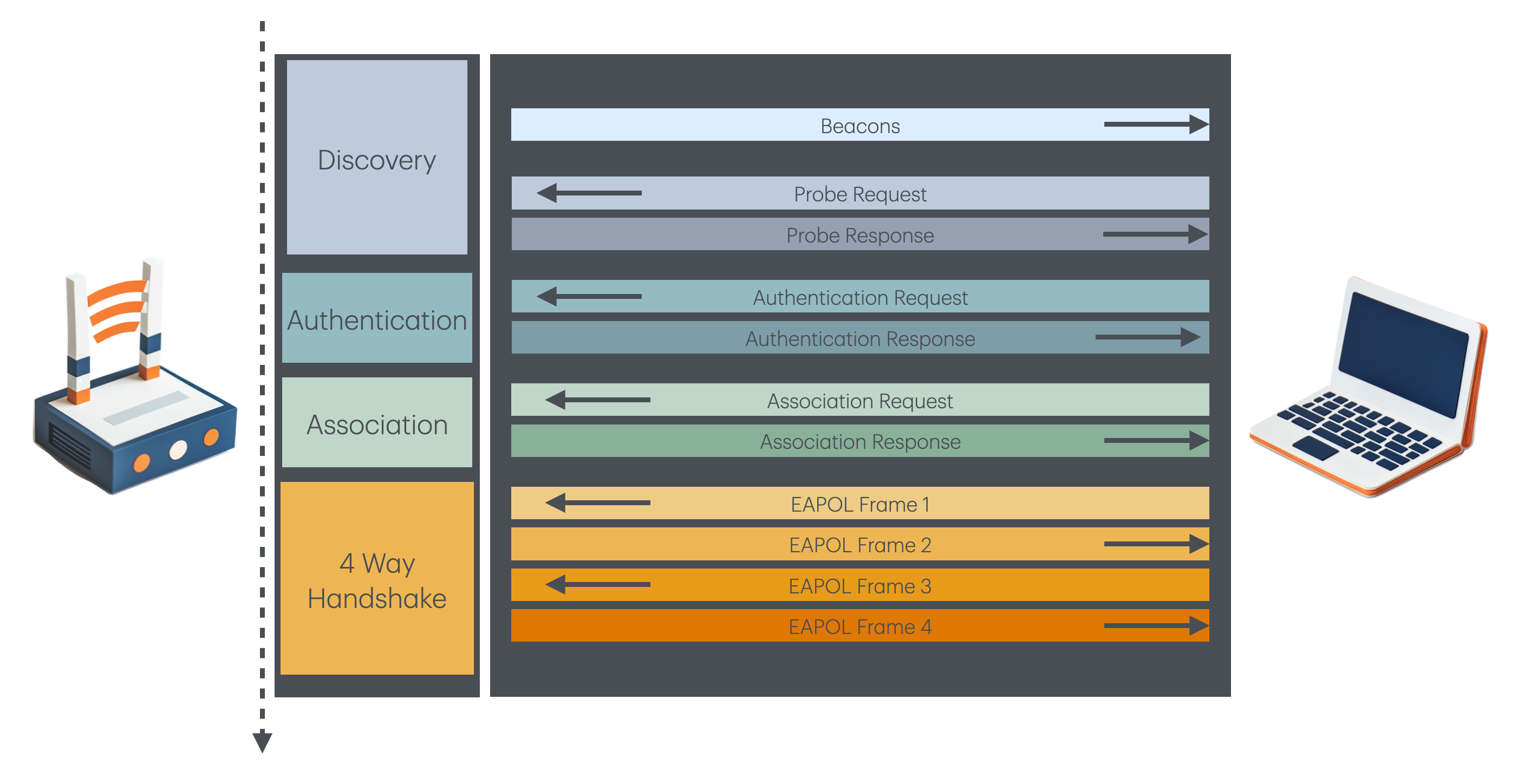
As a quick recap: when a station connects to an Access Point, it goes through a series of request/reply interactions. Several frames are in play including Probes, Authentication, Association, and finally Data frames with EAPOL. The EAPOL payloads perform all the fun cryptography with the passphrase for WPA2, WPA3, and 802.1X Authentication mechanisms.
