The Bitchat Update
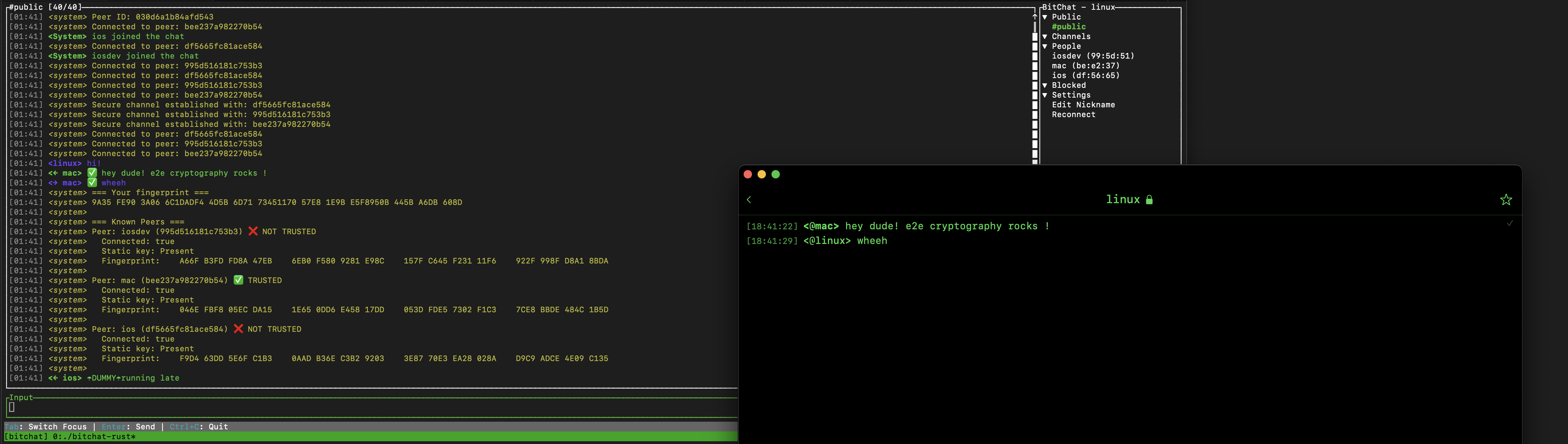
Bitchat Plugin Support on SPR
I've released a proof of concept for Bitchat running on Linux, along with a plugin configuration for SPR!
Background
Since we last wrote about Bitchat, the security response for Bitchat been pretty much perfect. Jack quickly added prominent warnings that Bitchat was in development, and very quickly (as in within a week or so), the protocol moved to use Noise Encryption, providing strong security guarantees. Not long after Bitchat made it to the App Store. And even more impressively a little while later support for Nostr made it in. Recently I got a patch in for a small security fix for handling plaintext DMs.