SPR Tailscale
Introducing SPR-TailScale
We've released a new iteration of the TailScale integration for SPR! This plugin was put together with @willy_wong.

We've released a new iteration of the TailScale integration for SPR! This plugin was put together with @willy_wong.

What a year it's been for the Secure Programmable Router (SPR) project! We've made great strides in empowering users to take control of their networks, prioritize privacy, and unlock network configurability. Let's dive right into the highlights of 2023 and peek at what's in store for the future.
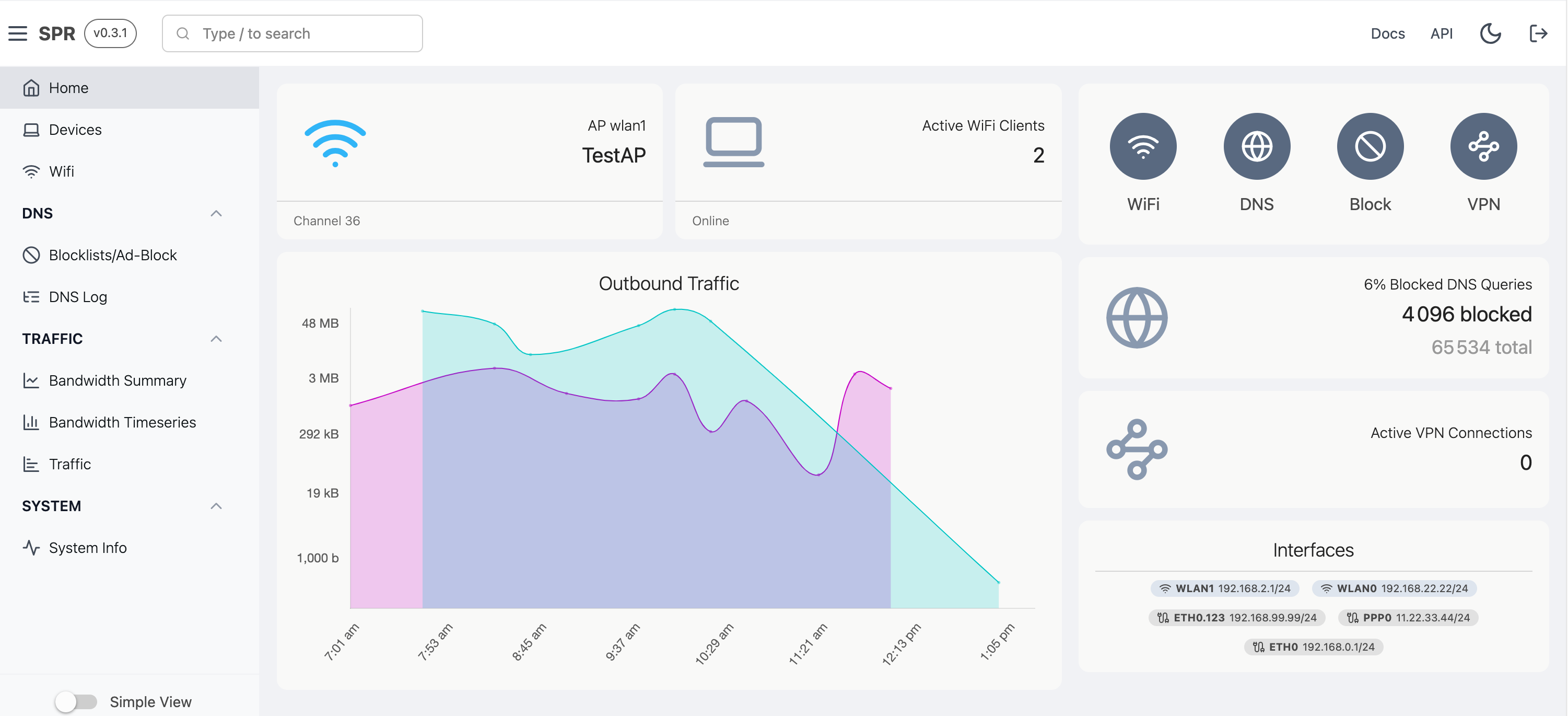
This post has become a guide which is being kept up to date, check it out!
In this post we'll show how PLUS members can add a mitmproxy plugin to their SPR setup,
and then use the Programmable Firewall (PFW) plugin to redirect traffic through mitmproxy with DNAT forwarding.
We do not need to configure our clients with proxy settings to point to mitmproxy, or rewrite DNS responses,
since we are using the PFW feature to do the redirection.