Editor's note:
The Turtles WiFi challenges are a series of ctf-style problems concerning network and wifi security skills.
The tasks were a bit challenging, and invovled a combination of WiFi Cracking and exploring how WPA Authentication works,
against a custom Access point using Salsa20 instead of AES.
Axel Souchet has kindly shared his writeup with us, which we share below.
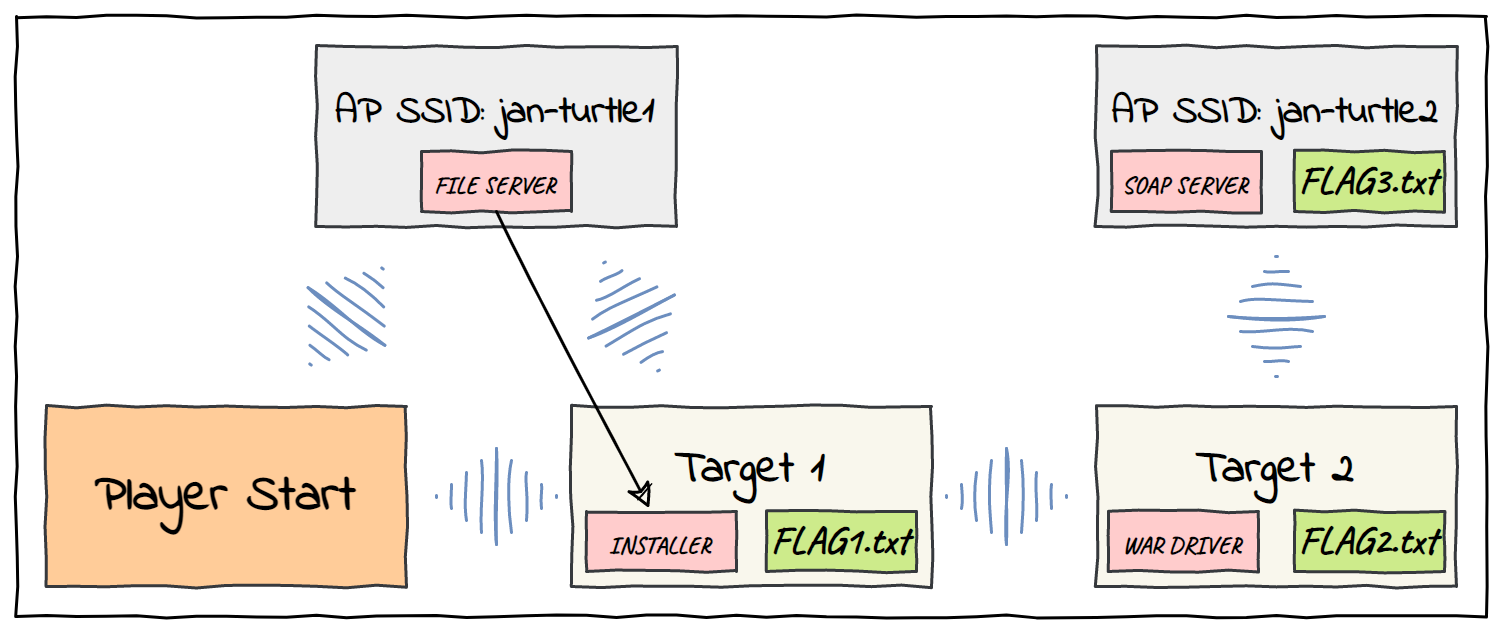
Turtles: Virtual WiFi Hacking Challenges - March 2023
Introduction
The older I get, the more fascinated I have become with the world surrounding me; I ask myself all the time 'how does this thing work uh 🤔?'. It is both fun and rewarding for me to understand the world a bit better. This is also a great way to be constantly humbled by the magic that surrounds us 🌈
Although I enjoy the process of learning how things work, there are millions of things that I interact with daily, that I know so little about; embarrassing.
Heck, how does WiFi work I thought? Because I know that I learn best by getting my hands dirty, I decided to try to solve a few challenges as an introduction. That is why I decided to check-out the March Turtle challenge 🙂
If you want to play at home, you can find the challenges on Github and one the SPR website:
You can participate either directly from your browser via an impressive emulated Linux environment or you can self-host the challenge by cloning the turtles-march-2023 repository and follow the instructions. I chose to self-host the challenges as it made it easier to debug for me.